Western companies in region bear brunt of Petya virus
SHANGHAI — A cargo terminal at a bustling Mumbai port lurched to a stop. Threatening text filled computer screens at a chocolate factory in Tasmania. The Australian offices of a multinational law firm told employees to avoid using email.
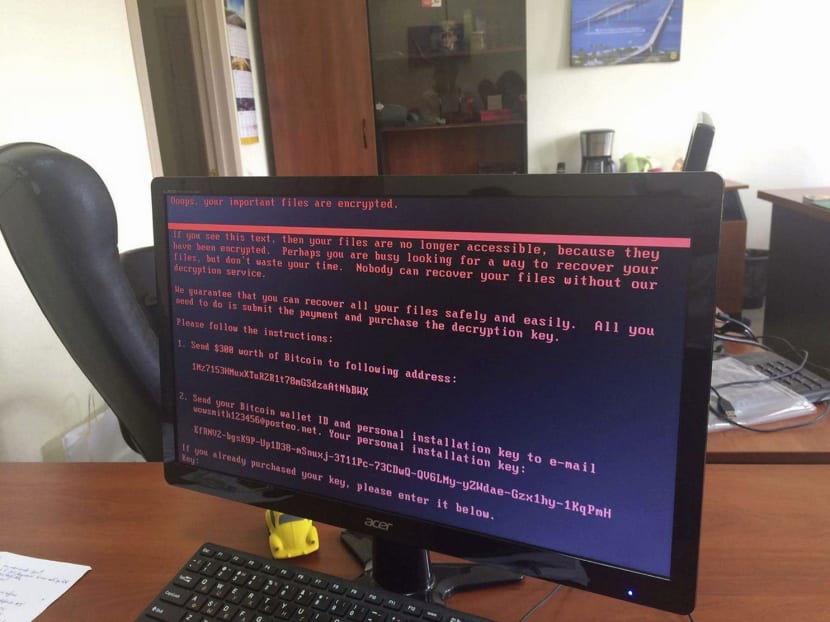
A computer displaying a warning notice, after a cyber attack at an office in Ukraine on Tuesday. Experts said the malware that hit computers was similar to a virus called Petya, which was first identified last year. The attack was judged by some experts to be more dangerous as it could spread across networks via a single affected computer. Photo: AP
SHANGHAI — A cargo terminal at a bustling Mumbai port lurched to a stop. Threatening text filled computer screens at a chocolate factory in Tasmania. The Australian offices of a multinational law firm told employees to avoid using email.
The Asia-Pacific region grappled yesterday with a cyber attack that struck Europe and the United States the day before. It was the second time in two months that hackers tried to shake down computer users around the globe by threatening to delete their data unless they paid up.
Yet the spread appeared somewhat limited in Asia yesterday as compared with a similar attack in May, when the software called WannaCry introduced the term “ransomware” to much of the world. The reason the cyber attack was less widespread was not immediately clear, though experts expressed doubt that the world had learned its lesson and properly prepared for an era of increasingly common global hacking attacks.
Like the WannaCry attack last month, computers struck by the virus displayed a message that said its data had been encrypted and demanded a ransom — in this case, US$300 (S$420) — to decrypt it.
Experts said the malware that hit computers on Tuesday was similar to a virus called Petya, which was first identified last year. The attack was judged by some experts to be more dangerous because it could spread across networks via a single affected computer.
The global scope of the attack underlines the power of a cache of National Security Agency (NSA) hacking tools that were leaked to the public. The new attack makes use of the same NSA tools that were used during the WannaCry episode, along with two other methods to promote its spread, according to researchers at the computer security firm Symantec.
A fuller picture of the impact could still emerge in coming days. But local companies and government offices appeared less affected, notably in places such as China, which were harder hit by the WannaCry bug in May.
Reports from Asia suggested that many of the companies hit were the local arms of European and American companies struck on Tuesday.
So far, the cyber attacks have generated just over US$9,000 in ransom payments, a figure that is likely to steadily rise over the coming days.
In Mumbai, the terminal that shut down was operated by AP Moller-Maersk, the Danish shipping giant, which said on Tuesday that it had been hit by the malware.
In a statement, the Indian port authorities said they were taking steps to relieve congestion, such as finding places to park stranded cargo. The attack shut the terminal down on Tuesday afternoon.
On the Australian island of Tasmania, computers in a Cadbury chocolate factory owned by Mondelez International, the American food company, displayed the ransomware message, according to local news media.
“We continue to work quickly to address the current global IT outage across Mondelez International and to contain any further exposure to our network,” said a spokeswoman for the company, adding that it was not clear when the company’s systems would be back up.
The virus also spread to the Australian branches of DLA Piper, a law firm with offices around the world. The law firm warned clients it was dealing with a “serious global cyber incident” and said it had taken down its communications as a precaution.
The Australian government has urged companies to install security updates and to isolate any infected computers from their main networks.
Asia most likely avoided major difficulties not because computers there are frequently updated, but because the attack itself targeted businesses in Ukraine, Russia and Poland, according to a post from the cyber security firm Kaspersky Lab. According to the report, Ukraine, Russia, Poland, Italy and Germany were the countries most affected by the attack.
Across Asia many computers run outdated or pirated versions of Windows and are particularly vulnerable to malware. During the WannaCry attack, both India and China were hard hit because many computer systems had not been upgraded.
So unwilling are companies in China to pay for security software that Qihoo 360 uses a business model that offers free security software, and then makes money off advertising. The company used the newest attack as a marketing opportunity: It said it was offering a worldwide anti-ransomware service, and if it failed to stop an attack, it would pay the ransom.
However, experts caution that paying the ransom may not help restore the computer. THE NEW YORK TIMES