Malware used by SingHealth cyber attackers ‘uniquely tailored, had not been observed elsewhere’
SINGAPORE — The hackers behind the SingHealth cyber attack snuck into its network in August last year, nearly a year before stealing the data of 1.5 million patients, the Committee of Inquiry (COI) looking into the attack heard on Friday (Oct 5).

The attackers’ skill and sophistication was one of three key factors that led to the breach, the Cyber Security Agency concluded in its public incident response report on the SingHealth incident.
SINGAPORE — The hackers behind the SingHealth cyber attack snuck into its network in August last year, nearly a year before stealing the data of 1.5 million patients, the Committee of Inquiry (COI) looking into the attack heard on Friday (Oct 5).
The attacker gained a foothold through an unpatched front-end computer at Singapore General Hospital, likely through a phishing email. He or she then stayed dormant for four months.
After successfully striking from June 27 to July 4, the attacker tried again on July 19 to re-enter the public healthcare cluster’s network.
This was a day before the Government broke the news of Singapore’s worst cyber attack to the public, and efforts to contain the threat and prevent a repeat attack were in full swing by then.
The suspicious activity — which showed the attacker had established more than one foothold in the network — was nipped in the bud.
The July 19 attempt prompted the Cyber Security Agency (CSA) to recommend that the Integrated Health Information Systems (IHiS, the Ministry of Health’s IT arm) implement Internet surfing separation.
STEALTH AND SKILL
The modus operandi and skillfulness of the hacker was the focus of Friday’s public hearing by the four-member COI.
The attackers’ skill and sophistication was one of three key factors that led to the breach, the CSA concluded in its public incident response report on the incident.
The other two factors — a vulnerability with SingHealth’s IT systems and a coding flaw in the Sunrise Clinical Manager database application — were covered in public hearings held last month.
“The tools, techniques and procedures, as well as some of the malware that the attacker used, fit the profile of an Advanced Persistent Threat (APT) group that CSA has previously encountered in other investigations,” said the agency.
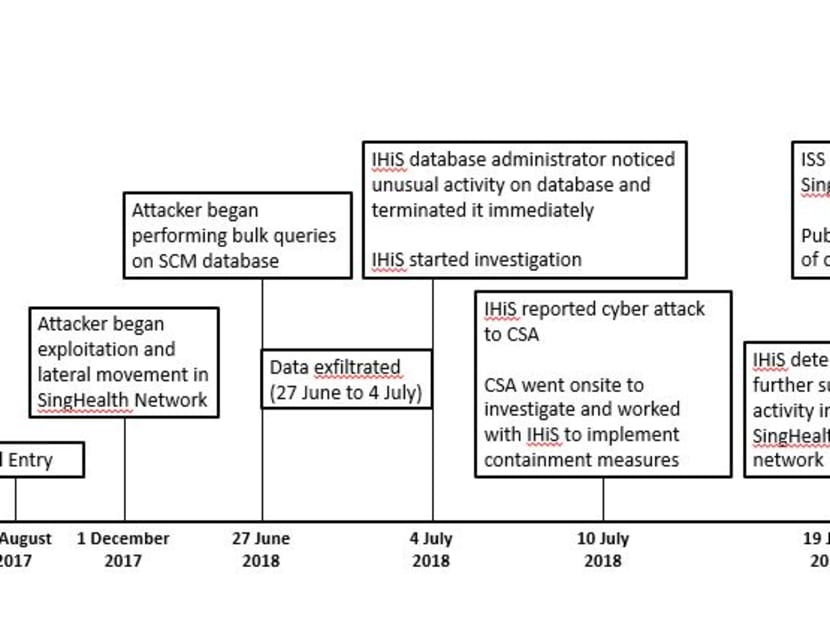
After gaining access on Aug 23 last year, the “disciplined” attacker only began in December to stealthily infect other workstations with malware, said Solicitor-General Kwek Mean Luck, who presented key findings of the report at the hearing.
This was discovered through forensic investigations, which showed signs of call-backs to an overseas command and control server.
The attacker exploited a benign tool built into Windows, called PowerShell, to install the malware and gain further credentials for entry into servers.
PowerShell, while a useful tool for computer technicians for task automation and configuration management, is increasingly used by cyber attackers as it has no signature files and thus would escape detection by anti-virus software, according to tech sites.
“The malware was customised, uniquely tailored to the targeted systems, and had not been observed elsewhere,” said the CSA in its report.
In fact, when CSA sent the malware sample to a “leading anti-virus company” for analysis, the company initially indicated the malware to be benign.
The attacker worked his way laterally in the network for another six months before finally gaining the credentials to access what COI chairman Richard Magnus called the “crown jewel” — the Sunrise Clinical Manager database holding electronic medical records.
He or she moved in a “targeted manner”, planning his route in the network and only compromising “selected computers” necessary to access, copy and transfer data from the database.
Between May and June, the attacker used compromised administrator accounts to remotely log in to Citrix servers — a bridging system — at the Singapore General Hospital. One of the administrator accounts had a weak password (P@ssw0rd) that could be easily decrypted.
At this point, the attacker had not obtained credentials to log in to the database, as seen through multiple failed attempts over days using non-existent user accounts or accounts that had insufficient privileges.
The attacker was likely to have obtained the correct log-in credentials to the Sunrise Clinical Manager database through one of the Citrix servers at the Healthcare Data Centre, which hosts the medical records. He or she likely exploited a loophole in the database application, which was discovered in 2014 by a former IHiS employee who was sacked for unethical conduct. IHiS’ top management, however, did not order an investigation of the loophole.
Using this crucial vulnerability, the hacker then launched the attack. Among the 1.5 million patients who had their personal data stolen, 160,000 of them including Prime Minister Lee Hsien Loong also had their outpatient medication data extracted.
SingHealth’s connection to the Internet, while serving operational needs, created an avenue of entry and exit for the attacker, said CSA in its report, which Mr Magnus said the committee is inclined to accept.
HEAD HONCHOS TO TESTIFY NEXT
In the wake of the cyber attack, IHiS disabled PowerShell on all end-user machines on July 13.
IHiS and CSA reset the masterkey account (which has full access to the SingHealth’s entire domain) twice.
This was to invalidate any existing access authentication tokens — or “golden tickets” — to the domain that the attacker might have created when entering the system.
IHiS also mandated password changes at end-user machine and database applications, and implemented Internet surfing separation for all healthcare clusters.
The CSA alerted the 10 other critical information infrastructure sectors — such as aviation, and banking and finance — of newly discovered indicators of compromise. It instructed them to scan their systems for signs of the attacker and recommended other security measures, such as disabling the unnecessary use of Powershell.
The COI will next focus on cybersecurity measures in place at the time of the attack, and IT governance frameworks.
The head honchos of the organisations involved are expected to testify at the end of the month, and some hearings will be open to the public.
Witnesses include IHiS chief executive Bruce Liang, SingHealth group chief information officer Benedict Tan, SingHealth group chief executive Ivy Ng, her deputy Kenneth Kwek and IHiS director of cyber security governance Chua Kim Chuan.
The COI is expected to submit a report of its findings by the end of the year.
Sign up for TODAY's WhatsApp service. Click here: