Robot vacuum cleaners can be used by hackers to 'spy' on private conversations: NUS study
SINGAPORE — Your robot vacuum cleaner could be picking up private conversations along with the dust and dirt in your home.
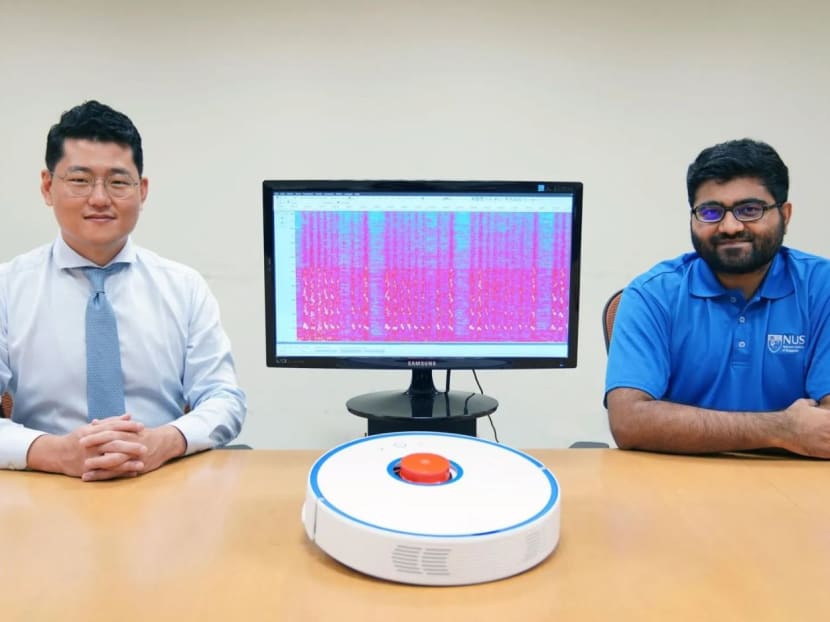
A research team led by Assistant Professor Jun Han from the Department of Computer Science at NUS Computing has demonstrated that the Lidar sensor atop a robot vacuum cleaner can be repurposed as a tool to spy on private conversations at home or in the office.
SINGAPORE — Your robot vacuum cleaner could be picking up private conversations along with the dust and dirt in your home.
Computer scientists from the National University of Singapore (NUS) have demonstrated how a common robot vacuum cleaner and its built-in light detection and ranging (Lidar) sensor could be used to "spy" on private conversations, the university said on Monday (Dec 7).
The method, called LidarPhone, repurposes the Lidar sensor that a robot vacuum cleaner normally uses for navigating around a home into a laser-based microphone to eavesdrop on private conversations.
The research team, led by Assistant Professor Jun Han and his doctoral student Sriram Sami, managed to recover speech data with "high accuracy", said NUS.
“The proliferation of smart devices — including smart speakers and smart security cameras — has increased the avenues for hackers to snoop on our private moments," said Mr Sami.
"Our method shows it is now possible to gather sensitive data just by using something as innocuous as a household robot vacuum cleaner. Our work demonstrates the urgent need to find practical solutions to prevent such malicious attacks."
HACKERS CAN LEARN CREDIT CARD DETAILS, SENSITIVE INFORMATION
The core of the LidarPhone “attack method” is the Lidar sensor, a device which emits an invisible scanning laser in order to create a map of its surroundings.
By reflecting lasers off common objects, such as a dustbin or a takeaway bag, located near a person’s computer speaker or television soundbar, the research showed that hackers could obtain information about the original sound that made the objects’ surfaces vibrate.
“Using applied signal processing and deep learning algorithms, speech could be recovered from the audio data, and sensitive information could potentially be obtained,” said NUS.
In their experiments, the researchers used a common robot vacuum cleaner with two sources of sound — the voice of a person reading out numbers played from a computer speaker and music clips from television shows played through a television soundbar.
The team collected more than 19 hours of recorded audio files and passed them through "deep learning algorithms" that were trained to either match human voices or identify musical sequences.
“The system was able to detect the digits being spoken aloud, which could constitute a victim’s credit card or bank account numbers. Music clips from television shows could potentially disclose the victim’s viewing preferences or political orientation,” said NUS.
The system achieved a classification accuracy rate of 91 per cent when recovering spoken digits and a 90 per cent accuracy rate when classifying music clips. These results are "significantly higher" than a random guess of 10 per cent, said NUS.
The NUS scientists also experimented with common household materials to test how well they reflected the Lidar laser beam and found that the accuracy of audio recovery varied between different materials — the best material for reflecting the laser beam was a glossy polypropylene bag, while the worst was glossy cardboard.
NUS students Dai Yimin and Sean Tan Rui Xiang, as well as Assistant Professor Nirupam Roy from the University of Maryland, contributed to the research. The research was presented at the Association for Computing Machinery's Conference on Embedded Networked Sensor Systems (SenSys 2020) on Nov 18, where the team clinched the Best Poster Runner Up Award.
INTERNET CONNECTED DEVICES POSE PRIVACY RISKS
To prevent Lidars from being misused, people with robot vacuum cleaners are advised to not connect them to the Internet.
The NUS team also recommends that Lidar sensor manufacturers incorporate a mechanism that cannot be overridden to prevent the internal laser from firing when the Lidar is not rotating.
“In the long term, we should consider whether our desire to have increasingly ‘smart’ homes is worth the potential privacy implications," said Asst Prof Han.
"We might have to accept that each new Internet-connected sensing device brought into our homes poses an additional risk to our privacy, and make our choices carefully.”
The team is working on applying these LidarPhone findings to autonomous vehicles, which also use Lidar sensors.
This technology could be used to eavesdrop on conversations happening in nearby cars through minute vibrations of the windows, said NUS.
The researchers are also looking into the vulnerability of active laser sensors found on the latest smartphones, which could reveal further privacy issues, the university added. CNA
For more stories like this, visit cna.asia.