Surge in Singapore-linked ‘botnet drones’, used by cyber criminals to hack into household devices: Report
SINGAPORE — As more people worked from home last year and more businesses went digital, authorities detected a sharp rise in botnet drones with Singapore internet protocol (IP) addresses, signalling that hackers are stepping up their attacks on home and office devices that are hooked up to the internet.

An annual report of the Cyber Security Agency of Singapore said that there had been a general increase in cyber threats in Singapore.
- The Cyber Security Agency of Singapore saw a total of 9,080 cases in 2020 related to cyber threats
- This was up from 8,491 cases in 2019 and 4,977 cases in 2018
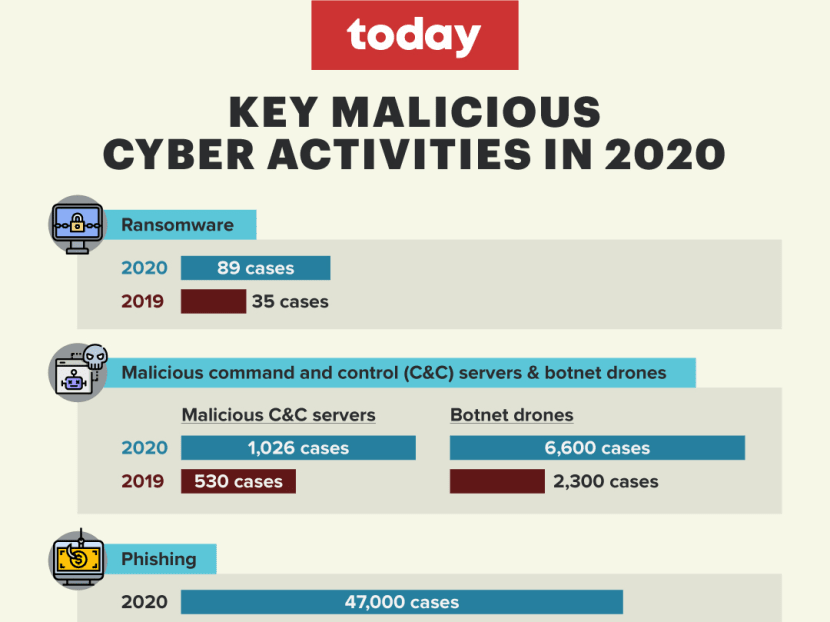
- It saw 1,026 malicious command and control servers hosted here, a 94 per cent jump from 2019
- Cyber crime remains a key concern, the police said, for it accounts for 43 per cent of overall crimes reported in 2020
- Website defacements fell 43 per cent last year from 2019
SINGAPORE — As more people worked from home last year and more businesses went digital, the authorities detected a sharp rise in botnet drones with Singapore internet protocol (IP) addresses, signalling that hackers are stepping up their attacks on home and office devices that are hooked up to the internet.
These could include everything from mobile phones and laptops to baby monitors and smoke detectors, experts said, warning that the rise in such attacks means that users should be more vigilant about the security of their devices.
Mr Ali Fazeli, an information security officer at Singapore-based Infinity Forensics, said that a botnet is a “network or collection of internet connected devices that are infected by malware and remotely controlled by the hacker”.
He said that a botnet drone (not a flying device) is a “computer malware that first infects and compromises the target computer and then connects the target computer into the botnet network”.
The near trebling of detected botnet drones with Singapore IP addresses — up from 2,300 daily in 2019 to 6,600 daily in 2020 on average — was one finding of an annual report by the Cyber Security Agency of Singapore (CSA) on the cyber landscape here. The report was released on Thursday (July 8).
An IP address allows computers to send and receive information and can be used to identify a computer’s location.
Aside from botnet drones, CSA reported a steep increase in other types of cyber threats such as ransomware and online scams last year.
CSA’s computer emergency response team saw a total of 9,080 cases in 2020 that were related to cyber threats such as ransomware incidents and online scams. Comparatively, there were 8,491 cases in 2019 and 4,977 cases in 2018.
BOTNET DRONES AND SERVERS
Last year, CSA observed 1,026 malicious command and control servers hosted in Singapore — a 94 per cent jump from the 530 command and control servers reported in 2019. These servers are used alongside botnet drones by cyber criminals.
Mr Gary Gardiner, head of security engineering for Asia Pacific and Japan at Check Point Software Technologies, a cyber security solutions provider, explained how botnet drones and command and control servers work using an analogy.
“Think about it from a military perspective. The command and control is the general sitting there telling the army of botnets what to do,” he told TODAY.
“The botnet drones will talk to the command and control server and ask its next command and then act on that. The commands can be anything from running a ransomware to stealing information or to upload information that is found on the device or the network that it is connected to.”
Mr Ian Hall, head of client services for Asia Pacific at Synopsys Software Integrity Group, told TODAY that the recent rise of botnet drones and malicious command and control servers reflected the success of criminals benefiting from this sort of activity.
“I don’t think that a week goes by without some new attack being published in the mainstream media — be it ransomware, distributed denial-of-service (DDOS) attack or something else. This kind of success means that the malicious actors are benefiting financially and therefore others want to get a piece of this pie,” he said.
Experts said that botnet drones are mainly used to target Internet-of-Things (IoT) devices.
Mr Lim Yihao, a principal intelligence adviser at United States-based cyber-security firm Mandiant, said that IoT is a term for smart devices that can connect to the internet, such as medical devices and home appliances.
With the “ever increasing number of devices that are connected to the internet with IoT devices growing in popularity every year”, it is another reason why botnet drones and malicious command and control servers are on the rise, Mr Hall said.
He also said that IoT devices are not being built with security in mind, which means applying security patches on them is not necessarily easy.
“The pandemic, I believe, has contributed to the increasing attack surface as more individuals stay home and also rely on remote working, telehealth and other means to remain socially distanced,” Mr Hall added.
Mr Lim said that the exact manner in which IoT devices are compromised depends on the kind of malware that is infecting them.
“In certain cases, the IoT device will become another ‘bot’ or ‘zombie’ as part of the wider botnet for DDOS attacks on targets — which usually indicates an abnormally high number of devices are trying to access one website at a single point of time, leading to the website crashing and malfunctioning,” he said.
Hackers may wish to gain access to everyday devices to listen into private conversations or compromise the victim’s privacy in other ways, Mr Gardiner said.
Mr Lim said that footage from hacked home cameras have even been leaked onto pornographic websites.
In order to protect IoT devices from being hacked, he advises online users to “ensure all IoT devices are not using default password credentials” and to “do periodic system reboot or firmware upgrade to get the latest (security) patches against known vulnerabilities”.
Mr Fazeli advised against opening spam emails and suspicious files.
FINDINGS FROM REPORT
Ransomware
Last year, 89 ransomware cases were reported — a 154 per cent surge from the 35 reported cases in 2019
These mostly affected small- and medium-sized enterprises (SMEs) from the manufacturing, retail and healthcare sectors
There was a significant increase in local ransomware cases said to be likely influenced by the global upswing in ransomware
Cyber crime
Last year, 16,117 cyber-crime cases were reported, compared with 9,349 cases in 2019
Cyber crime remains a key concern, the police said, for it accounted for 43 per cent of overall crimes reported last year
Online cheating is a top cyber-crime category here — 12,251 cases reported last year compared with 7,580 cases in 2019
This 62 per cent increase can be attributed to the rapid growth of e-commerce, the proliferation of community marketplace platforms and social media platforms as people carried out more online transactions due to the pandemic
Phishing
About 47,000 unique Singapore-hosting phishing uniform resource locators (URLs) were observed last year, a slight fall of 1 per cent compared with the 47,500 URLs seen in 2019
Phishing scams involve criminals impersonating other people to try to obtain the victim’s banking or other details
Though last year saw a surge in Covid-19-related phishing campaigns globally, the overall volume of malicious phishing URLs in Singapore was comparable to that of 2019
There were 4,700 cases of malicious URLs spoofing local entities and services that were in greater demand during Singapore’s circuit breaker or semi-lockdown period in April and May 2020, inclusive of online rental and payment portals. These were attributed to the pandemic
WEBSITE DEFACEMENTS
Last year, 495 ".sg" websites were defaced — a significant decline of 43 per cent from the 873 cases reported in 2019
Victims of website defacements were SMEs; no government websites were affected
The significant decrease last year is consistent with global trends — activists groups could have chosen other methods with a larger potential reach such as social media to embarrass their victims and attract visibility for their causes